🦥 About Me
Hello there! I am a 2nd-year Ph.D. student (advised by Prof. Zhenkai Liang) at School of Computing, National University of Singapore (NUS). I received my Master of Computing degree from NUS, and B.E. degree in Information Security (advised by Prof. Zhijun Ding) at Tongji University. I worked as cloud-computing security researcher in the Xingyun Lab of NSFOCUS from 2019 to 2022. My research interests mainly lie in the interactions of system security, program analysis, and AI, with a focus on developing practical and effective solutions to improve the security of various real-world systems. Specifically, my work centers around vulnerability intelligence, including vulnerability discovery, analysis, assessment, and defense, by leveraging and advancing various techniques, including program analysis, fuzzing, and AI. In addition, I also have a strong interest in interdisciplinary research that bridges technical and societal perspectives, such as AI governance and the social implications of cybersecurity risks and incidents.
Motto: Life is like carrying a heavy burden on a long journey; one must not be hasty.
🔥 News
- Sep 2025 🎉 Our work on vulnerability assessment for software supply chains (VPSS) is accepted at ASE 2025!
- Aug 2025 🏅 FlowFusion wins the Distinguished Paper Award at USENIX Security 2025!
- Aug 2025 🎉 Our MCP dataset (MCPCorpus) is accepted at ASE 2025 Tool Demonstrations!
- Jun 2025 🚩 I have passed my Qualifying Exam and am now a Ph.D. candidate!
- Apr 2025 🎉 KernJC is presented at BlackHat Asia 2025!
- Jan 2025 🎉 Our work on PHP fuzzing (FlowFusion) is accepted at USENIX Security 2025!
- Oct 2024 🏅 KernJC wins the Best Practical Paper Award at RAID 2024!
- Aug 2024 🎉 Our vulnerability intelligence dataset (VulZoo) is accepted at ASE 2024 Tool Demonstrations!
- Jun 2024 🎉 Our work on kernel vulnerability reproduction (KernJC) is accepted at RAID 2024!
🌋 Featured Publications
SYSTEM & SOFTWARE SECURITY
[ASE 2025] Propagation-Based Vulnerability Impact Assessment for Software Supply Chains
Bonan Ruan, Zhiwei Lin, Jiahao Liu, Chuqi Zhang, Kaihang Ji, Zhenkai Liang
40th IEEE/ACM International Conference on Automated Software Engineering
@article{ruan2025accurate,
title={An Accurate and Efficient Vulnerability Propagation Analysis Framework},
author={Ruan, Bonan and Lin, Zhiwei and Liu, Jiahao and Zhang, Chuqi and Ji, Kaihang and Liang, Zhenkai},
journal={arXiv preprint arXiv:2506.01342},
year={2025}
}
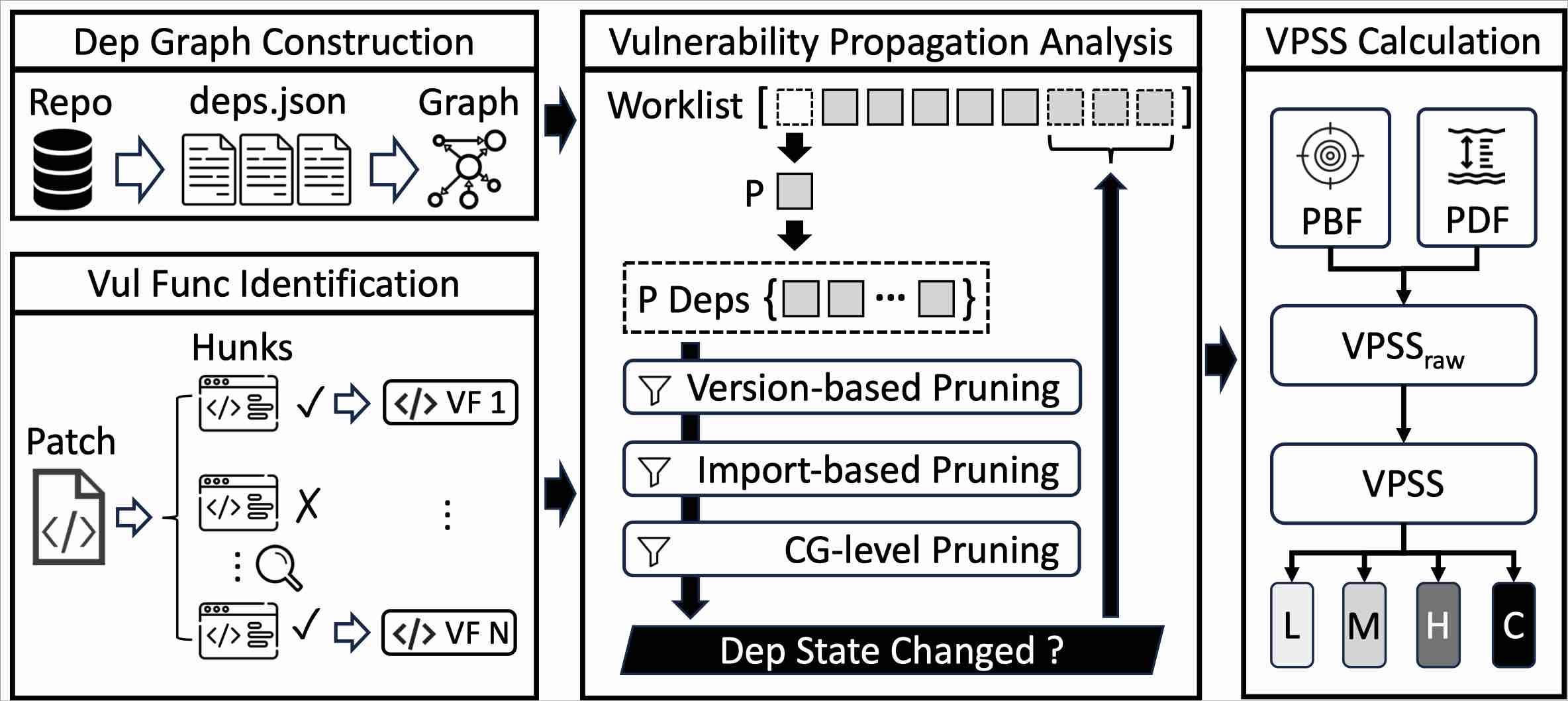
Identifying the impact scope and scale is critical for software supply chain vulnerability assessment. However, existing studies face substantial limitations. First, prior studies either work at coarse package-level granularity—producing many false positives—or fail to accomplish whole-ecosystem vulnerability propagation analysis. Second, although vulnerability assessment indicators like CVSS characterize individual vulnerabilities, no metric exists to specifically quantify the dynamic impact of vulnerability propagation across software supply chains. To address these limitations and enable accurate and comprehensive vulnerability impact assessment, we propose a novel approach: (i) a hierarchical worklist-based algorithm for whole-ecosystem and call-graph-level vulnerability propagation analysis and (ii) the Vulnerability Propagation Scoring System (VPSS), a dynamic metric to quantify the scope and evolution of vulnerability impacts in software supply chains. We implement a prototype of our approach in the Java Maven ecosystem and evaluate it on 100 real-world vulnerabilities. Experimental results demonstrate that our approach enables effective ecosystem-wide vulnerability propagation analysis, and provides a practical, quantitative measure of vulnerability impact through VPSS.
[USENIX Security 2025] Fuzzing the PHP Interpreter via Dataflow Fusion
Yuancheng Jiang, Chuqi Zhang, Bonan Ruan, Jiahao Liu, Manuel Rigger, Roland Yap, Zhenkai Liang
34th USENIX Security Symposium
🏅 Distinguished Paper Award
@inproceedings{jiang2025fuzzing,
title={Fuzzing the PHP Interpreter via Dataflow Fusion},
author={Jiang, Yuancheng and Zhang, Chuqi and Ruan, Bonan and Liu, Jiahao and Rigger, Manuel and Yap, Roland HC and Liang, Zhenkai},
booktitle={34th USENIX Security Symposium (USENIX Security 25)},
pages={6143--6158},
year={2025}
}
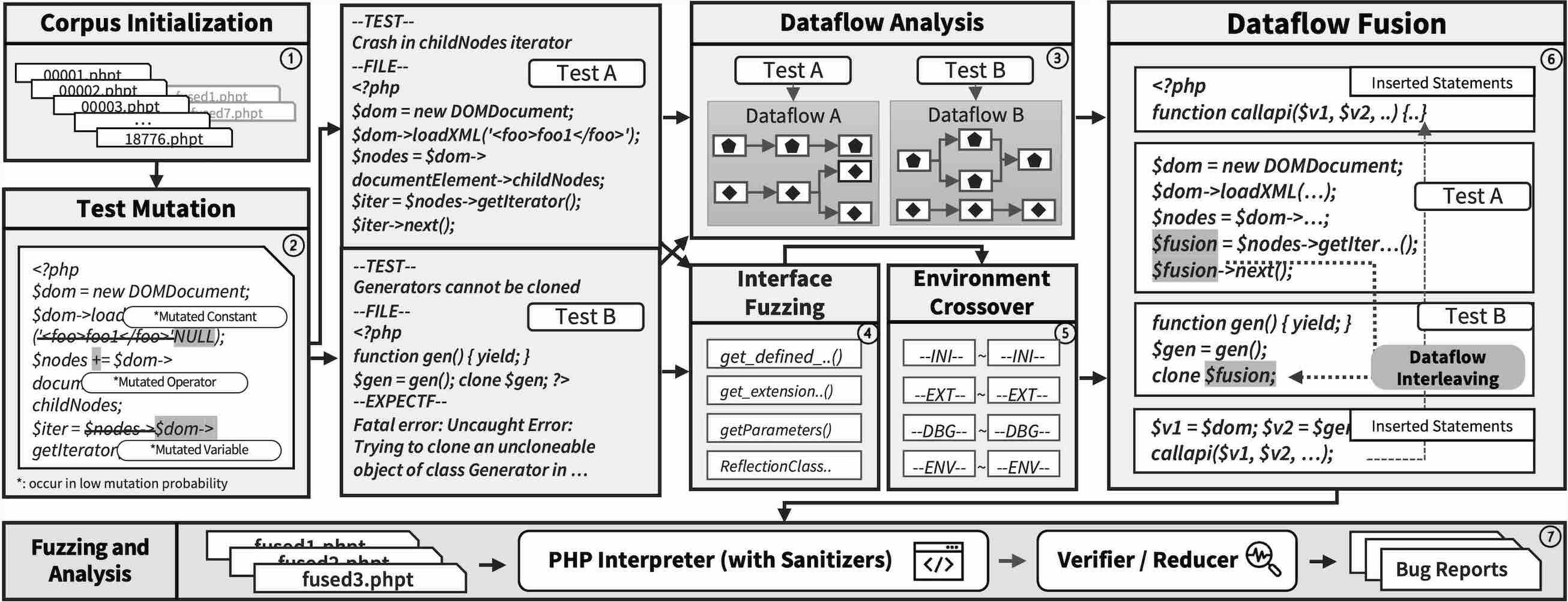
PHP, a dominant scripting language in web development, powers a vast range of websites, from personal blogs to major platforms. While existing research primarily focuses on PHP application-level security issues like code injection, memory errors within the PHP interpreter have been largely overlooked. These memory errors, prevalent due to the PHP interpreter's extensive C codebase, pose significant risks to the confidentiality, integrity, and availability of PHP servers. This paper introduces FlowFusion, the first automatic fuzzing framework to detect memory errors in the PHP interpreter. FlowFusion leverages dataflow as an efficient representation of test cases maintained by PHP developers, merging two or more test cases to produce fused test cases with more complex code semantics. Moreover, FlowFusion employs strategies such as test mutation, interface fuzzing, and environment crossover to increase bug finding. In our evaluation, FlowFusion found 158 unknown bugs in the PHP interpreter, with 125 fixed and 11 confirmed. Comparing FlowFusion against the official test suite and a naive test concatenation approach, FlowFusion can detect new bugs that these methods miss, while also achieving greater code coverage. FlowFusion also outperformed state-of-the-art fuzzers AFL++ and Polyglot, covering 24% more lines of code after 24 hours of fuzzing. FlowFusion has gained wide recognition among PHP developers and is now integrated into the official PHP toolchain.
[RAID 2024] KernJC: Automated Vulnerable Environment Generation for Linux Kernel Vulnerabilities
Bonan Ruan, Jiahao Liu, Chuqi Zhang, Zhenkai Liang
27th International Symposium on Research in Attacks, Intrusions and Defenses
🏅 Best Practical Paper Award
@inproceedings{ruan2024kernjc,
title={Kernjc: Automated vulnerable environment generation for linux kernel vulnerabilities},
author={Ruan, Bonan and Liu, Jiahao and Zhang, Chuqi and Liang, Zhenkai},
booktitle={Proceedings of the 27th International Symposium on Research in Attacks, Intrusions and Defenses},
pages={384--402},
year={2024}
}
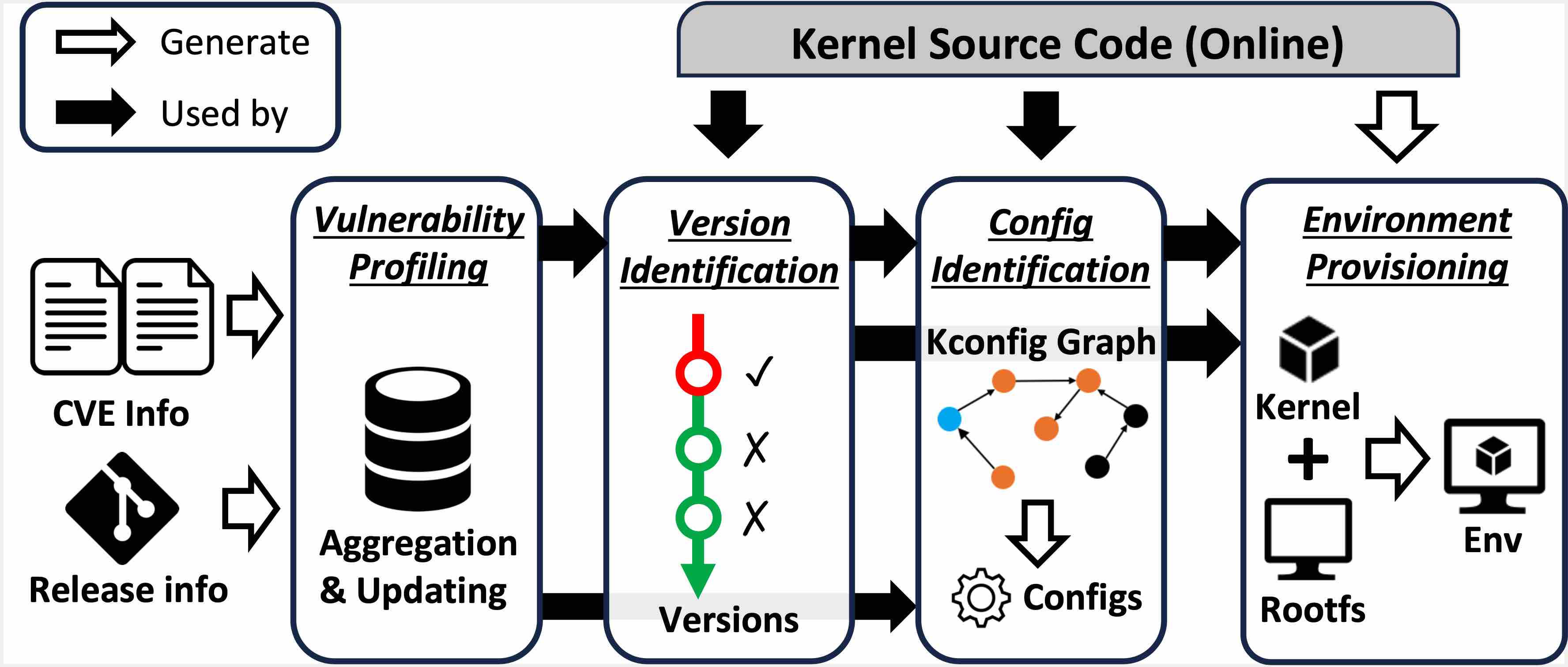
Linux kernel vulnerability reproduction is a critical task in system security. To reproduce a kernel vulnerability, the vulnerable environment and the Proof of Concept (PoC) program are needed. Most existing research focuses on the generation of PoC, while the construction of environment is overlooked. However, establishing an effective vulnerable environment to trigger a vulnerability is challenging. Firstly, it is hard to guarantee that the selected kernel version for reproduction is vulnerable, as the vulnerability version claims in online databases can occasionally be incorrect. Secondly, many vulnerabilities cannot be reproduced in kernels built with default configurations. Intricate non-default kernel configurations must be set to include and trigger a kernel vulnerability, but less information is available on how to recognize these configurations.
To solve these challenges, we propose a patch-based approach to identify real vulnerable kernel versions and a graph-based approach to identify necessary configs for activating a specific vulnerability. We implement these approaches in a tool, KernJC, automating the generation of vulnerable environments for kernel vulnerabilities. To evaluate the efficacy of KernJC, we build a dataset containing 66 representative real-world vulnerabilities with PoCs from kernel vulnerability research in the past five years. The evaluation shows that KernJC builds vulnerable environments for all these vulnerabilities, 32 (48.5%) of which require non-default configs, and 4 have incorrect version claims in the National Vulnerability Database (NVD). Furthermore, we conduct large-scale spurious version detection on kernel vulnerabilities and identify 128 vulnerabilities that have spurious version claims in NVD. To foster future research, we release KernJC with the dataset in the community.
LLM-BASED AGENT SYSTEM SECURITY
[Preprint] When MCP Servers Attack: Taxonomy, Feasibility, and Mitigation
Weibo Zhao, Jiahao Liu, Bonan Ruan, Shaofei Li, Zhenkai Liang
arXiv 2025
@article{zhao2025when,
title={When MCP Servers Attack: Taxonomy, Feasibility, and Mitigation},
author={Zhao, Weibo and Liu, Jiahao and Ruan, Bonan and Li, Shaofei and Liang, Zhenkai},
journal={arXiv preprint arXiv:2509.24272},
year={2025}
}
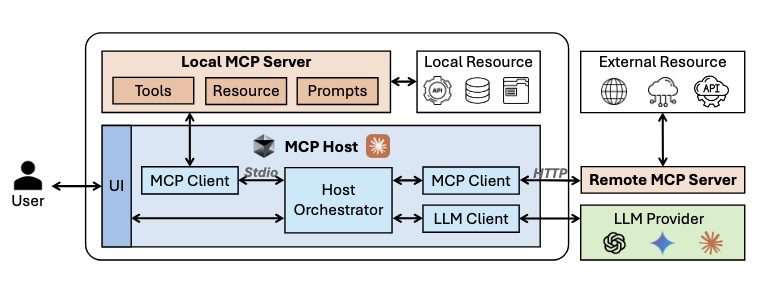
Model Context Protocol (MCP) servers enable AI applications to connect to external systems in a plug-and-play manner, but their rapid proliferation also introduces severe security risks. Unlike mature software ecosystems with rigorous vetting, MCP servers still lack standardized review mechanisms, giving adversaries opportunities to distribute malicious implementations. Despite this pressing risk, the security implications of MCP servers remain underexplored. To address this gap, we present the first systematic study that treats MCP servers as active threat actors and decomposes them into core components to examine how adversarial developers can implant malicious intent. Specifically, we investigate three research questions: (i) what types of attacks malicious MCP servers can launch, (ii) how vulnerable MCP hosts and Large Language Models (LLMs) are to these attacks, and (iii) how feasible it is to carry out MCP server attacks in practice. Our study proposes a component-based taxonomy comprising twelve attack categories. For each category, we develop Proof-of-Concept (PoC) servers and demonstrate their effectiveness across diverse real-world host-LLM settings. We further show that attackers can generate large numbers of malicious servers at virtually no cost. We then test state-of-the-art scanners on the generated servers and found that existing detection approaches are insufficient. These findings highlight that malicious MCP servers are easy to implement, difficult to detect with current tools, and capable of causing concrete damage to AI agent systems. Addressing this threat requires coordinated efforts among protocol designers, host developers, LLM providers, and end users to build a more secure and resilient MCP ecosystem.
DATASET & Benchmark
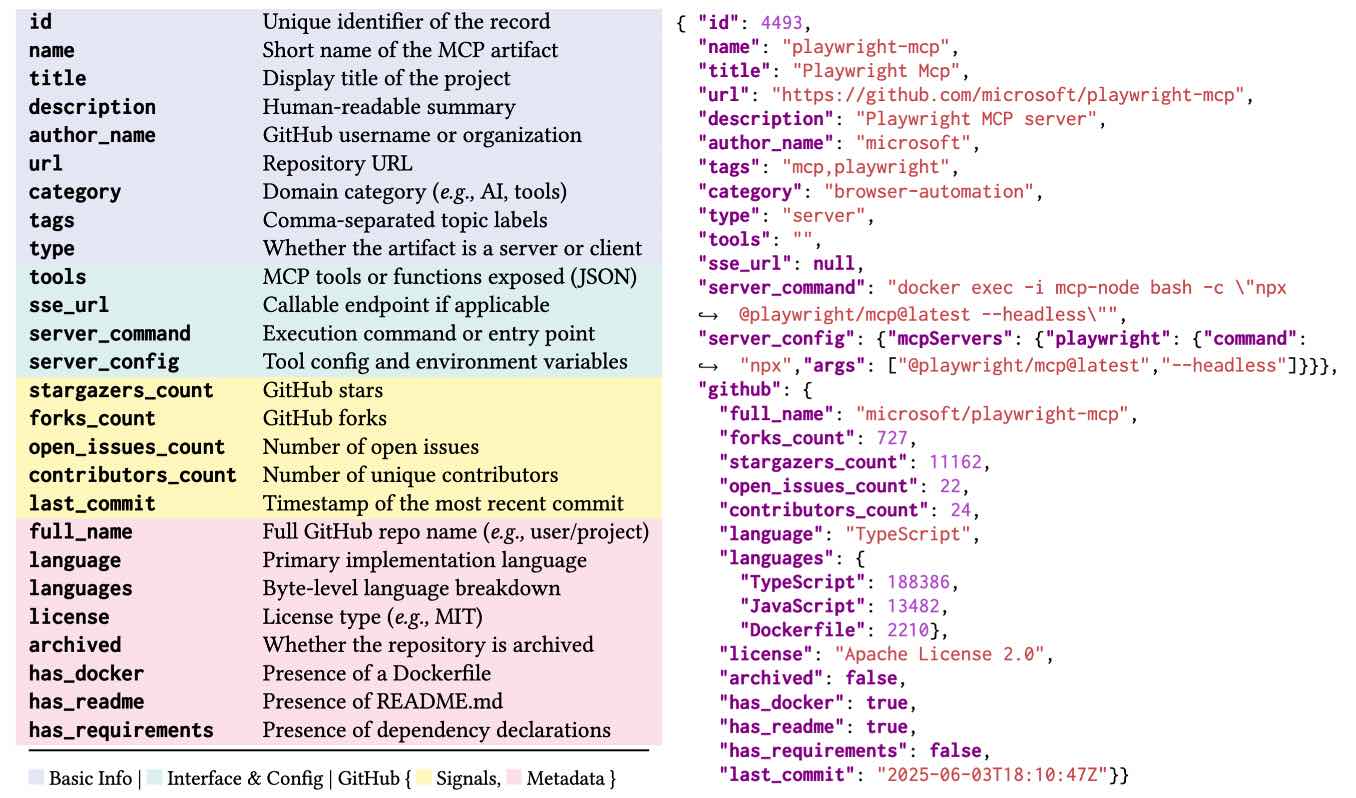
[ASE 2025] A Large-Scale Evolvable Dataset for Model Context Protocol Ecosystem and Security Analysis
Zhiwei Lin, Bonan Ruan, Jiahao Liu, Weibo Zhao
40th IEEE/ACM International Conference on Automated Software Engineering, Tool Demonstrations
@article{lin2025large,
title={A Large-Scale Evolvable Dataset for Model Context Protocol Ecosystem and Security Analysis},
author={Lin, Zhiwei and Ruan, Bonan and Liu, Jiahao and Zhao, Weibo},
journal={arXiv preprint arXiv:2506.23474},
year={2025}
}
The Model Context Protocol (MCP) has recently emerged as a standardized interface for connecting language models with external tools and data. As the ecosystem rapidly expands, the lack of a structured, comprehensive view of existing MCP artifacts presents challenges for research. To bridge this gap, we introduce MCPCorpus, a large-scale dataset containing around 14K MCP servers and 300 MCP clients. Each artifact is annotated with 20+ normalized attributes capturing its identity, interface configuration, GitHub activity, and metadata. MCPCorpus provides a reproducible snapshot of the real-world MCP ecosystem, enabling studies of adoption trends, ecosystem health, and implementation diversity. To keep pace with the rapid evolution of the MCP ecosystem, we provide utility tools for automated data synchronization, normalization, and inspection. Furthermore, to support efficient exploration and exploitation, we release a lightweight web-based search interface. MCPCorpus is publicly available at: https://github.com/Snakinya/MCPCorpus.
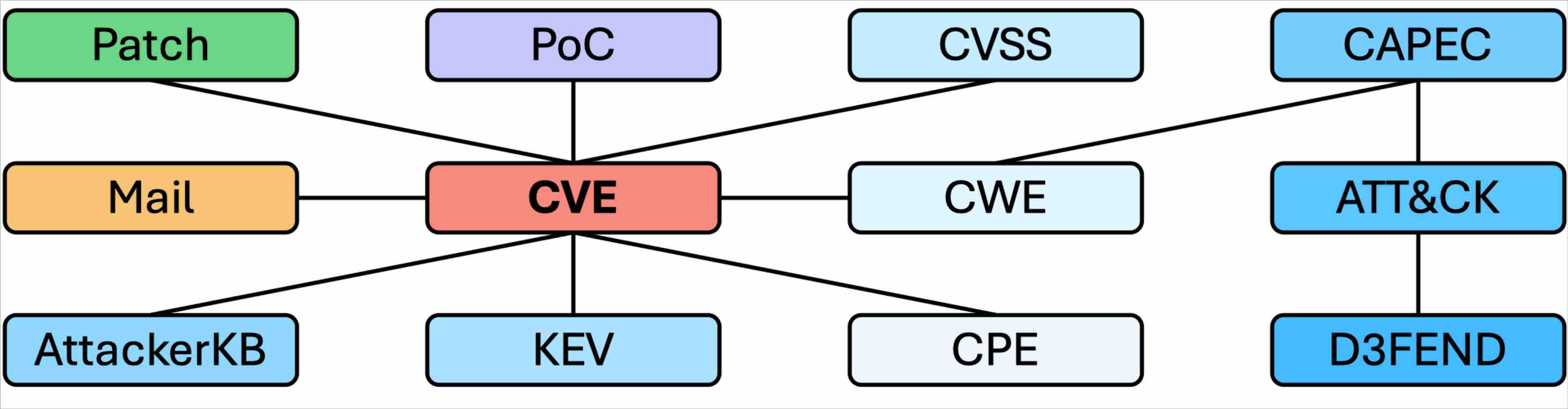
[ASE 2024] VulZoo: A Comprehensive Vulnerability Intelligence Dataset
Bonan Ruan, Jiahao Liu, Weibo Zhao, Zhenkai Liang
39th IEEE/ACM International Conference on Automated Software Engineering, Tool Demonstrations
@inproceedings{ruan2024vulzoo,
title={Vulzoo: A comprehensive vulnerability intelligence dataset},
author={Ruan, Bonan and Liu, Jiahao and Zhao, Weibo and Liang, Zhenkai},
booktitle={Proceedings of the 39th IEEE/ACM International Conference on Automated Software Engineering},
pages={2334--2337},
year={2024}
}
Software vulnerabilities pose critical security and risk concerns. Many techniques are proposed to assess and prioritize vulnerabilities. To evaluate their performance, researchers often craft datasets from limited data sources, lacking a global overview of broad vulnerability intelligence. The repetitive data preparation process complicates the evaluation of new solutions. To solve this issue, we propose VulZoo, a comprehensive vulnerability intelligence dataset that covers 17 vulnerability data sources. We also construct connections among these sources, enabling more straightforward configuration and adaptation for different tasks. VulZoo provides utility scripts for automatic data synchronization and cleaning, relationship mining, and statistics generation. We make VulZoo publicly available and maintain it with incremental updates. We believe that VulZoo serves as a valuable input to vulnerability assessment and prioritization studies. The video is at https://youtu.be/EvoxQmUAHtw. The dataset is at https://github.com/NUS-Curiosity/VulZoo.
📚 Book Chapters
Cloud Native Security: Practice and Architecture
Wenmao Liu, Guolong Jiang, Ming Pu, Bonan Ruan, Xiaohu Ye
Beijing: China Machine Press. ISBN: 9787111691839. 2021.
Contributed Chapters: 3, 4, 14, and 16.
Douban |


🌵 Talks and Speeches
[BlackHat Asia 2025] KernJC: Automated Vulnerable Environment Generation for Linux Kernel Vulnerabilities
Abstract |
Video |
Slides |
WP |

Linux kernel vulnerability reproduction is a critical task in system security. To reproduce a kernel vulnerability, the vulnerable environment and the Proof of Concept (PoC) program are needed. Most existing research focuses on the generation of PoC, while the construction of environment is overlooked. However, establishing an effective vulnerable environment to trigger a vulnerability is challenging. Firstly, it is hard to guarantee that the selected kernel version for reproduction is vulnerable, as the vulnerability version claims in online databases can occasionally be incorrect. Secondly, many vulnerabilities cannot be reproduced in kernels built with default configurations. Intricate non-default kernel configurations must be set to include and trigger a kernel vulnerability, but less information is available on how to recognize these configurations.
To solve these challenges, we propose a patch-based approach to identify real vulnerable kernel versions and a graph-based approach to identify necessary configs for activating a specific vulnerability. We implement these approaches in a tool, KernJC, automating the generation of vulnerable environments for kernel vulnerabilities. To evaluate the efficacy of KernJC, we build a dataset containing 66 representative real-world vulnerabilities with PoCs from kernel vulnerability research in the past five years. The evaluation shows that KernJC builds vulnerable environments for all these vulnerabilities, 32 (48.5%) of which require non-default configs, and 4 have incorrect version claims in the National Vulnerability Database (NVD). Furthermore, we conduct large-scale spurious version detection on kernel vulnerabilities and identify 128 vulnerabilities that have spurious version claims in NVD. To foster future research, we release KernJC with the dataset in the community.
[KCon 2022] Dilemma: runC’s Achilles’ Heel
Abstract | Video | Slides | WP
This talk explores the exploitation of vulnerabilities in container runtimes, focusing on two critical issues: CVE-2019-5736 in runC and CVE-2022-0847 (Dirty Pipe) in the Linux kernel. These vulnerabilities highlight the risks inherent in containerized environments, such as privilege escalation and host compromise, which pose significant threats to modern infrastructure security. The presentation begins with an analysis of Dirty Pipe, a Linux kernel vulnerability that allows unprivileged processes to overwrite data in read-only files, enabling code injection into privileged processes. We demonstrate how this exploit facilitates container escape when combined with the runC vulnerability, which allows attackers to overwrite the runC binary on the host system, achieving root access. Through live demonstrations, we showcase advanced exploitation techniques, including ELF manipulation, memory injection via Dirty Pipe, and stealthy post-exploitation persistence. We also examine practical mitigations, such as hardening runC and kernel-level defenses, to secure containerized environments. This comprehensive analysis provides valuable insights for security researchers and practitioners into detecting, mitigating, and understanding vulnerabilities in container infrastructures.
[OID Asia 2021] Metarget: Auto-construction of Vulnerable Cloud Native Infrastructure
This talk introduces Metarget, an innovative framework designed for the automatic construction of vulnerable cloud-native environments. By facilitating the deployment of multi-layered, vulnerable infrastructures, Metarget enables researchers and ethical hackers to efficiently simulate complex attack scenarios ranging from container exploitation to cluster-level persistence. The presentation highlights offensive methodologies in cloud-native security, including real-world case studies such as post-penetration attacks against Kubernetes clusters. Using Metarget, we explore vulnerabilities like CVE-2020-15257 and CVE-2020-8559, demonstrating how attackers can achieve lateral movement and full cluster compromise. Additionally, we showcase k0otkit, a post-penetration persistence technique for Kubernetes, emphasizing its role in automating and advancing offensive security research. Through a detailed analysis of offensive strategies, this talk illustrates how tools like Metarget accelerate defensive innovations, paving the way for more robust cloud-native security practices.
[CIS 2020] k0otkit: A Universal Manipulation Technique in Post-Penetration against Kubernetes
This presentation introduces k0otkit, a universal post-penetration control technique for Kubernetes (K8s) clusters. By leveraging Kubernetes-native features such as DaemonSets, Secrets, and container injection, k0otkit provides attackers with rapid, covert, and persistent control over large-scale clusters. This talk explores the evolution of k0otkit through its various iterations, highlighting advancements in stealth, persistence, and efficiency, including the adoption of fileless attack techniques and encrypted communication. The discussion outlines a typical Kubernetes penetration process, emphasizing container escape, privilege escalation, and lateral movement, leading to full cluster control. Through live demonstrations, we showcase how k0otkit exploits Kubernetes vulnerabilities, automates reverse shell deployment, and achieves seamless cluster-wide compromise. Finally, the talk concludes with key defensive strategies to mitigate these risks, including implementing Pod security policies, detecting anomalous container behavior, and protecting against fileless attacks. This comprehensive analysis offers valuable insights for both offensive and defensive Kubernetes security research.
👾 Patents
- CN111835768: A Method, Apparatus, Medium, and Device for Handling Security Incidents
- CN112035839: A Method and Apparatus for Detecting Race Condition Vulnerability Exploitation
- CN111831275: A Method, Server, Medium, and Device for Orchestrating Micro-Scenario Scripts
- CN112153049: An Intrusion Detection Method, Apparatus, Device, and Computer-Readable Medium
- CN115103362: A Method, Apparatus, and Device for Restoring 5G Network Element Call Sequences
🧲 Teaching Activities
- [2025 Fall] CS5231 System Security with Zhenkai Liang
- [2025 Spring] CS5321 Network Security with Zhenkai Liang
- [2024 Fall] CS5231 System Security with Zhenkai Liang
🎯 Vulnerabilities & Bugs Discovered
CVE-2024-50260 - sock_map: fix a NULL pointer dereference in sock_map_link_update_prog()






